Worker Privacy
Evaluating the Impact of Workplace Occupancy Technology
As offices reopen, they are relying on CoWorkr sensors and dynamic data to evaluate space usage, monitor occupancy levels, and worker behavior to ensure a safe working environment. CoWorkr technology is private, easy-to-use, maintain, and versatile. Stream usage data to consoles for easy monitoring of routine cleaning and sanitizing of shared office spaces and optimize your layout for maximum productivity.
Introduction
Offices around the globe are rolling out workplace occupancy technologies as a means to regain control of environments threatened by near-term issues of COVID-19 and longterm shifts in culture and worker behavior. These technologies are designed to provide space utilization data to workplace management on how workers occupy spaces for the purpose of creating a more efficient, productive, and safe workplace. While leveraging new tools for improving space management is a step in the right direction, many organizations may be too quick to adopt new technologies without considering significant factors surrounding worker privacy. In this blog post, we’ll look at why organizations are choosing workplace technologies, what tech makes up the current offerings, and how each one may impact worker privacy.
1.0 Why WorkPlace Occupancy Tech is Booming
1.1 Technology’s Response to Long-Term Shifts in the WorkPlace
It’s well known that today’s workplace — how it looks, feels, and performs — is vastly different than it was 10 years ago. The role of the workplace has shifted with the culture and tools buzzing within its walls. CoWorkr has observed a slow change across all industries as a response to new workplace demographics (baby boomers are now only 6%), available (mobile) technologies that allow for remote or flexible schedules, and other trends. As these changes are constantly evolving, it is often difficult for teams to wrap their hands around the trends and design for them. Workplace technologies exist to facilitate new working styles, such as flexible seating or hot-desking to drive wellness, efficiency, and productivity.
One major subset of workplace technologies that has become increasingly important is a software segment dedicated to helping manage dynamic spaces. “Dynamic spaces”, a concept spun out of the aforementioned changes that have impacted the traditional workplace. To understand why organizations need help managing dynamic spaces, take this scenario: A company today rarely expects all of its employees to report to the office on a daily basis and, when they do, their time is split between workstations, meeting rooms, collaborative spaces, phone booths, and other ad hoc spaces. This means the use of one space type may be significantly different from another based on the workers’ personalities, tasks, or other external factors. Most significantly, the workers need help interacting with dynamic space since, in many scenarios, they are required to search for available shared spaces and reserve and/or check-into them throughout the day.
The dynamism that comes with the modern worker’s day puts significant stress on those planning and maintaining their work environments. If you don’t know when workers are coming in the door, from where they’re working, or how long they’re staying, how is it possible to make any decisions on your workplace’s environment — the 2nd biggest expense behind staff? Companies like CoWorkr and other workplace sensor providers have built their businesses on the premise that autonomous and continuous occupancy data analysis is ultimately required to keep these environments operating efficiently on a day-to-day basis and serve as the foundation for improvements.
Historically, workplace technologies like sensor platforms and integrated workplace management systems (IWMS) used this occupancy data and associated analytics to inform strategy services. The occupancy real-time data was low-resolution and its requirements were minimal. Today, these technologies — now with the baseline assumption that all sensors operate in real-time and analytics are very granular — are capable of so much more.

Workplace Occupancy Data Powers Multiple Stakeholders
Workplace occupancy real-time data has become such an integral piece of CRE that it’s now seen as the heartbeat of the technologies that allow workers to interface with their environments. The demand for technology in the workplace has fueled the development of unique solutions for monitoring occupancy. Thanks to the evolution of hardware components, over the past 5 years, CoWorkr has leveraged a shift from high to low latency in sensor reporting, battery lifetimes exceeding their shelf lives, and the introduction of powerful machine learning to help derive occupancy counts from other sources of data.
1.2 Technology’s Response to New, Short-Term Shifts in the WorkPlace
While the workplace technology market that drives dynamic space use such as ABW or flexible environments has been slow to reach more conservative organizations, the spread of COVID-19 is forcing people to think of how their spaces can become more elastic — tightening the belt when utilization is low to keep workers engaged and flexing as workers return. With work-from-home and other flex policies having rolled out involuntarily, workplaces are at all-time low utilization levels. In turn, social distancing guidelines are forcing floor areas and space capacities to be reconfigured. These new issues are compounding atop the existing difficulties already faced by CRE teams.
If a workplace has a significant impact on the productivity of its employees and ultimately drives the growth for an organization, the gravity of maintaining this environment during or after an event like a pandemic is enormous. Even though, as of Q3 2020, the workplace is still yet to be occupied by many organizations around the world, we have observed a significant uptick in the requests for global deployments to tackle the post-COVID-19 environment. The scenario is pushing the workplace technology industry to new levels of demand.
Organizations are eager to discover and deploy workplace technologies that may be used to combat social distancing, the emotional perception of safety, and budget impacts of increased cleaning. For many, this is their first introduction to deploying technology that may be used to monitor the building occupancy and it’s no surprise that there are very few resources available to comparatively understand the techniques used and the impact it may have on the privacy of their workers.
2.0 How WorkPlace Occupancy Tech Differs
When thinking about workplace privacy, it’s important to consider the difference between how workers engage their everyday technology compared to something like an IoT or building platform. Typically, when we think of privacy, it may be a splash screen on a website requesting the collection of “cookies” or maybe an end-user license agreement that we accept as part of using an App. The act of receiving the notification and our acknowledgment is a part of an active or “participatory” technology process — it’s engaging and often involves continual updates or notifications which reminds us of the technology’s existence. Some may refer to this as opt-in tech, wherein users have the option to participate if they choose.
Passive, or “non-participatory” technologies, such as those deployed in physical spaces (e.g. sensor systems, building automation, and security controls) perform tasks without using an explicit user interface and without the ability for the general worker to opt-out. When a worker walks into their workplace, they’re agreeing to become one of the data points that informs the operation of the space and possibly the outcomes of other decisions made about the space and the staff that occupy them. Similar to browsing an app, under the pretense of workplaces deploying passive technologies, it’s very likely that many workers walk into private spaces unknowing that their presence is part of this data ecosystem.
Since workers do not directly engage with passive workplace technologies, for example, they can’t tell a security camera whether or not they agree to its ability to surveil their movements, organizations must be very respectful of worker privacy. Beyond simply how technology works and/or what it collects, one of the most important aspects for an organization to consider is how workers — without much insight — will perceive the technology. If there’s negative connotation created by technology, workers may develop new behaviors that disrupt routine and productivity.
3.0 Methods of Occupancy Data Collection
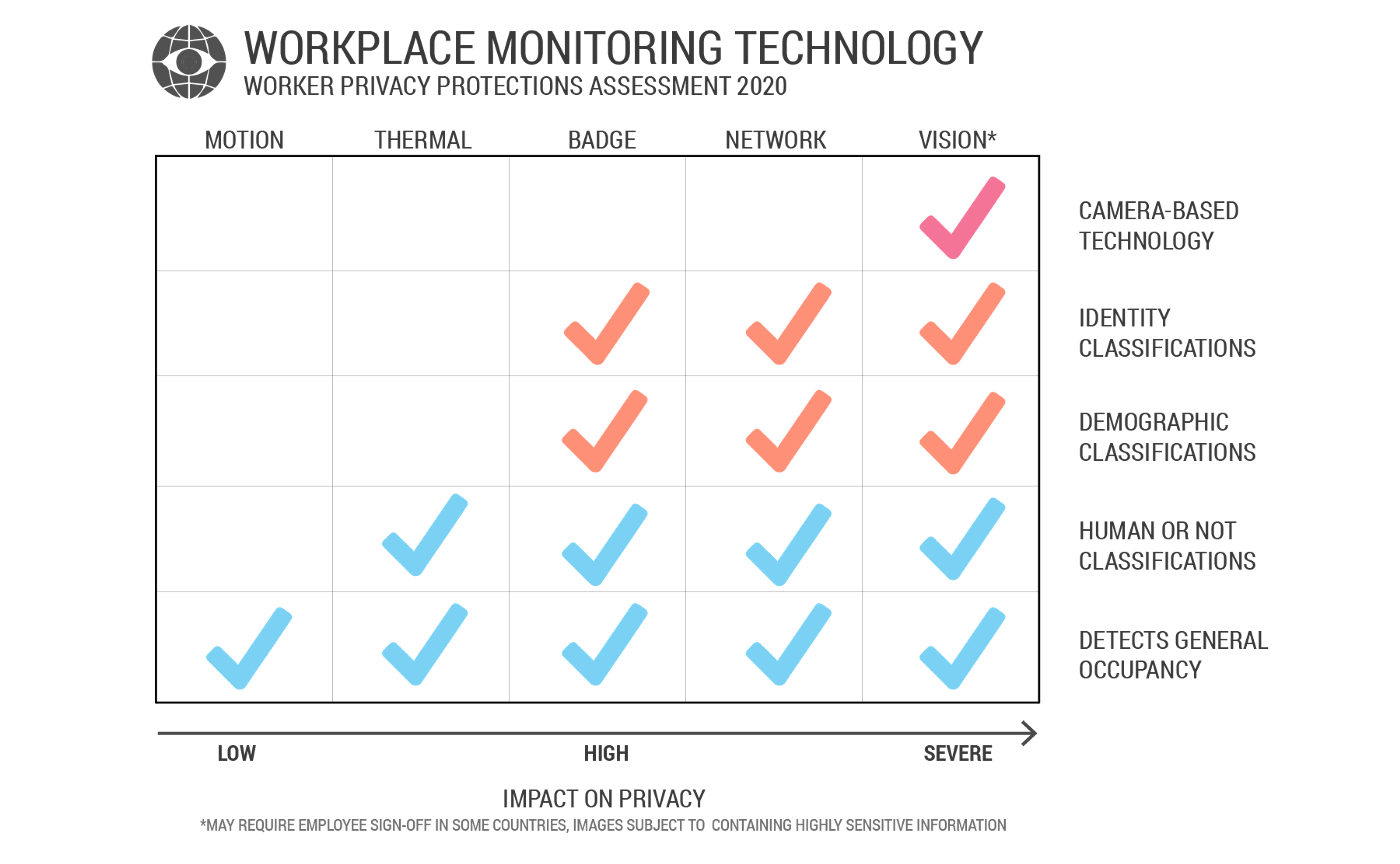
The various passive methods of occupancy data collection pose a sliding scale of impact on worker privacy.
3.1 Motion Sensing
An office is a relatively static environment. Objects, such as furniture, don’t necessarily move without the presence of a worker. This allows for using simple yet powerful infrared technologies to look for movement as a method of detecting occupancy. A single infrared sensor is generally used to monitor the use of a single space — a simple yet very important task. Using devices like CoWorkr’s WorkPoint sensor, organizations can get occupancy data for a variety of spaces without sacrificing cost or privacy.
Since infrared sensing alone has no ability to detect information beyond a motion event; it presents itself as one of the options with the lowest impact on worker privacy. These devices also have a very narrow scope of use, in that they’re very good at one task and cannot be modified to introduce new logic that may be used to increase the impact on privacy. The common use of motion sensing in workplaces as a method to control building systems, like lighting, also makes it a digestible type of technology to deploy.
3.2 Thermal Object Sensing
Thermal object sensing takes infrared sensing technology one step further and pairs a more high-definition infrared sensor with artificial intelligence. CoWorkr refers to this “Thermal object detection” or “Thermal”. Thermal sensing has many advantages in the spectrum of workplace occupancy detection devices given the human body — an inherently warm object — have a unique heat signature that’s easy to spot with infrared technology.
Thermal occupancy detection is most similar to using a camera (visible-light spectrum) to detect humans but instead of capturing a photograph with colors and shadows, the device captures infrared-light. This means the contents of the IR sensor are ambiguous, unlike a photograph — adding a level of security to infrared-based devices.
Another advantage IR has over using cameras and an AI that analyzes the contents of photographs is that it does not rely on colors or shading. For example, a human wearing all black and sitting on all black furniture makes the profile (object) of the human indistinguishable. Using thermal, the shape of the body is clearly distinguishable regardless of the colors or shadows of the visible scene.
Furthermore, an improvement in privacy for IR-based devices, at least in the example of CoWorkr’s thermal object detection, is that the actual processing of this information is done on the device itself. It does not require sending any information off the device itself for processing or “deep learning”.
Overall, thermal occupancy detection, when compared to camera-based devices, vastly limits the ability for the device to collect personally identifiable or private information like the demographics (age, race, gender) of the person, the type of work being performed, or even readable text in the scene. In the world of AI and object classification (the ability for the software to determine what’s present), the resources are evolving rapidly, becoming more advanced, and unfortunately becoming more invasive.
3.3 Badge Tracking
Identification badges are a common part of everyday workplace experiences. Depending on the style and security of an environment, badge access points may be located at only the main entry points, at every floor entry, or even at specific spaces that have been assigned to only specified workers. Badges, if in key-card form, use a Radio-frequency identification (RFID) technology that, when triggered by the electromagnetic interrogation pulse of a badge reader, transmit digital data back to the reader. Newer technologies are beginning to use software on mobile phones as a replacement for badges. In either scenario, an identity is determined during the transaction.
Beyond providing access to a space based on building level permissions, identity data from either the badge or phone is often aggregated by real estate or facility teams to understand how many workers and at what time enter a space. Unfortunately, since this data typically doesn’t mark the event of when a worker exits a space, it’s not useful beyond counting how many workers enter a space. Badge data cannot be used for utilization data.
From a privacy perspective, while this data is ultimately the definition of personally identifiable information (PII) given it contains IDs that link the workers’ name and other sensitive information, the act of a worker providing this information upon entrance to a space is considered to be a highly important aspect of building security and one that may protect them in the long run. Second to security, the fact that the PII collected is only attached to a single entry event and does not track an identity throughout the space gives worker peace of mind. If badging is deployed at high density across an office, the more opportunity the management has to track identities.
3.4 Network Monitoring
Once considered one of the most invasive methods of monitoring workers, WiFi or network monitoring tracks mac addressing (unique devices) coming on and off internal networks. Hypothetically, this means when a user brings a laptop or a mobile phone into a workplace and connects to the corporate network, that device is used to represent an occupant. The method of using network monitoring for deriving occupancy is questionable given some workers have multiple devices and a device that is connected to a network in a space doesn’t always mean there’s an individual present.
Historically, workers have been wary of this sort of technology since it quickly leads to other larger questions of if and how upper management is monitoring the use of their computers. Newer technology that deploys network monitoring APIs is thankfully doing more to protect worker privacy by implementing the anonymization of mac addresses and taking other precautionary measures.
3.5 Vision (Cameras)
The rise of OpenCV and other deep-learning-related AI paired with the reduced cost of small cameras is making vision-based occupancy detection technologies more prevalent. By analyzing the contents of camera images, a deep-learning AI model can draw quick conclusions as to what is taking place. In the case of human occupancy detection, an ai-powered device can identify humans that match other learned photos of humans. Vision devices are typically mounted to ceilings looking downwards but can also exist as software that is overlaid on existing security cameras or even teleconferencing device cameras used in meeting rooms.
Vision-based object detection is a very powerful tool that may be used not only for human occupancy detection but also for facial recognition, reading printed or handwritten text, and recognizing hundreds of different objects and object features. As an example, a “signs of life” metric derived from camera-based sensors is done by the AI detecting objects like notebooks, laptops, and other known worker tools. While this may be useful to understand what workers are doing — this exemplifies an overreaching technology that may have an overwhelming impact on worker privacy and behavior. These same types of devices, as well as AI-based software run on security cameras, have enormous privacy implications. As object detection and classification compound, we clearly see why they may be classified as one of the most invasive types of workplace technologies. Human occupancy detection can be easily paired with race, age, and gender classification — allowing devices to provide not only if someone is in front of the camera but also the demographics of the individual.
4.0 Privacy Impacts of Occupancy Monitoring
It’s undoubtedly true that individuals are comfortable giving away more private information today than ever before. The wave of social media platforms and other software that use personal data as a source of revenue is just getting larger and while companies require unequivocal consent from all users to do so, we all know that technology is collecting and exploiting more of our personal data than we ever imagined possible. This is why organizations around the world are forming strategies to help protect consumers from questionable business practices. When it comes to passive technologies, that workers are not actively engaging, it’s important to be even more sensitive to their needs.
Areas of concern for workers generally revolve around concepts of unauthorized or unknown surveillance and uncontrolled data generation. When distilled down, organizations must not only evaluate what type of data is collected and the impact it may have privacy but clearly communicate and disclose the use of technology to its workers. Such internal communications must be established prior to the deployment of monitoring technologies and the workers understand the nuances of the technology.
If there’s unauthorized access, for example, an ongoing hack wherein data is exposed, what’s to lose? Hacking a source that provides nothing more than useless unintelligible strings of data poses a very different outcome than a database of identities, images, or other PII.
Precursor questions to consider:
- Are workers comfortable with the level of information being captured?
- Are the devices deployed capable of capturing more information than workers may prefer?
- How will workers perceive a technology regardless of what it may actually do and will it alter their behavior?
- What’s the long term growth of this technology look like and do I morally approve of its potential?
5.0 Evaluation of Technology
5.1 Standards in Privacy
While the regulation of privacy is a relatively new task at hand for many organizations and governments, there are great frameworks now available for adoption. The General Data Protection Regulation (GDPR) set forth by the European Union, which took effect in 2018, one of the leading sets of privacy laws in the world has identified “Privacy by Design” (PbD) as a framework for evaluating the effective impact on privacy. A PbD methodology prioritizes privacy and data integrity early in the design process and throughout the development lifecycle of new products and services that involve collecting or processing personal data.
5.2 CoWorkr’s Privacy Evaluation
As an example of CoWorkr’s own evaluation of technology, when faced with choosing to develop devices that use infrared technologies rather than cameras (visible-light), the company opted to consult the Privacy by Design methodology as a primary source of guidance. A key PbD consideration when evaluating technologies is if a required task, e.g. detecting human presence, can be performed in a way that will not jeopardize the privacy of an individual. Our company deliberated, can the required data be as effectively collected by using a less invasive method?
 Example scene analysis using a vision-based device with AI (not CoWorker)
Example scene analysis using a vision-based device with AI (not CoWorker)
CoWorkr’s evaluation determined that both infrared sensors and cameras may be paired with software leveraging artificial intelligence to provide accurate and efficient human occupancy detection. Cameras, however, and their photographs can provide much more contentious information to an AI. Even if the technology intends on only using the camera’s images for the purpose of discreet occupancy data collection, we’d still be utilizing a technology that may be used (and perceived by workers) in a much different and damaging way.
5.3 Learning from Others
While the PbD methodology allowed for a guided path to explore CoWorkr’s options, there are other less structured alternatives. It’s also important to evaluate technologies just based on on-going public events and the failures of others. For the area of individual privacy and AI, there are many relevant ongoing conversations in the public regarding how to control its use.
“AI is a rare case where we need to be proactive about regulation instead of reactive. Because I think by the time we are reactive in AI regulation, it’s too late.”
We see lessons learned coming from top organizations down. IBM, Intel, and Microsoft have recently committed to no longer sell, support, or develop AI-based facial recognition technologies that may be used “for mass surveillance, racial profiling, violations of basic human rights and freedoms” to police. Even though the AI that was initially powering these programs was undoubtedly intended to only be helpful at incubation, they’ve created very real social issues amongst the communities where they’re deployed. This scenario of pushing a technology too soon and without enough testing is analogous to many situations ongoing with the release of AI-powered software.
In our own home, we can observe devices that clearly have no regard for privacy baked into their core functionality and design. New devices like the Amazon Alexa or Google Home offer an incredible voice recognition service by pairing natural language processing (AI), other service providers, and the internet. Ask for the weather, play a song, or read your emails — it just requires the device to listen to all of the nearby voices, 24/7. It’s an absurd trade-off of privacy for functionality that exemplifies what happens when there is no effective oversight provided to individuals.
6.0 Moving Forward
While we, as consumers or workers within an organization, must trust technology companies to be making the right choices with things we might not understand, regulations like GDPR and PbD, hackers, and technology figureheads will help highlight the potential issues. Since many technologies are relatively new, many institutions and governments are lagging in regulation. Weighing the impact on privacy is often left in the hands of the person using or the organization deploying the technology.
CoWorkr advocates for organizations to be proactive in addressing worker privacy by evaluating technology beyond general insight on how things work and into how it may impact worker behavior.